We are already familiar with the Auditing feature, which enables us to track user access to the system, monitor updates made to specific columns, retrieve previous column values before updates, identify record deletions, and much more. Audit logs can be viewed in the Audit History tab for a single record and in the Audit Summary view for all audited operations within a single environment.
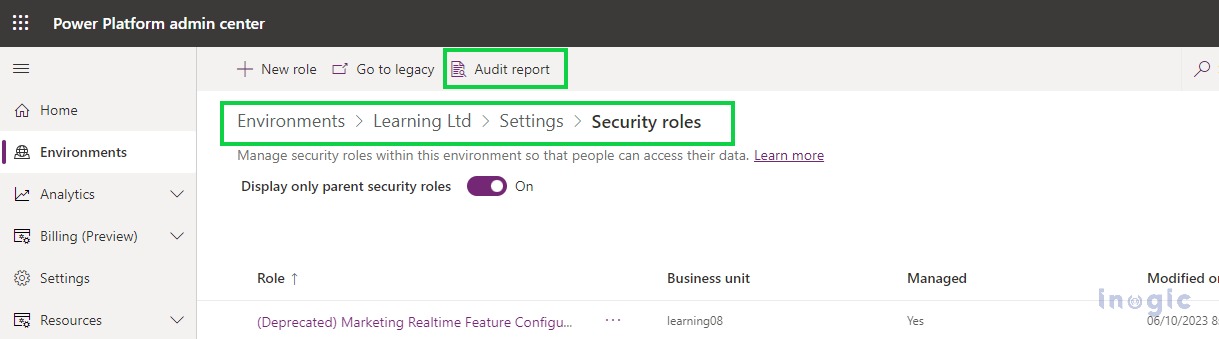
For the Security Role Entity, viewing audit history from the security role entity record itself was not possible till now. However, with the recent release, Microsoft added a button called Audit Report on the security role entity as well using which, you can easily view logs from the security role entity itself.
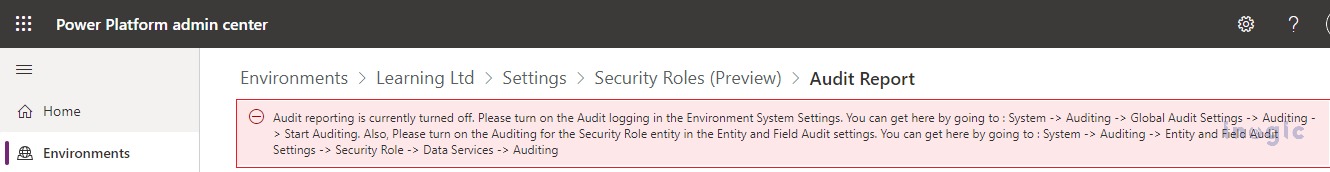
But if you have not enabled Audit Reporting and Auditing for the Security Role table, you will end up with the below error on clicking of Audit Report button-
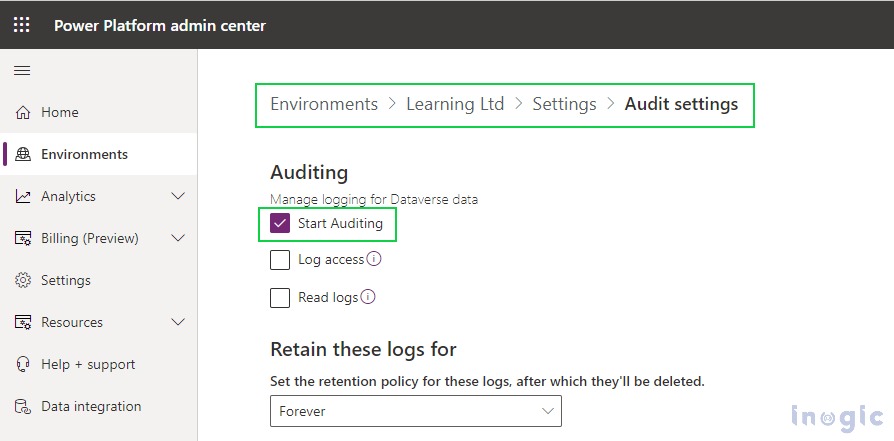
To enable Audit Reporting, navigate to Settings > Under Audit and logs, click on Audit Settings, and check the Start Auditing checkbox as shown below-
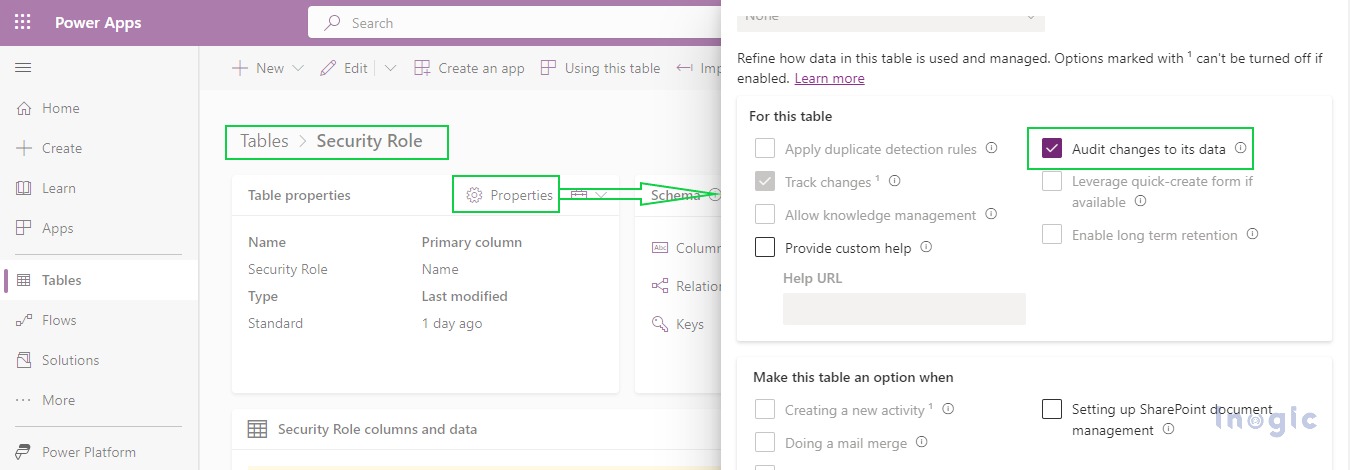
To enable Auditing for the Security Role table, in the Security role entity table properties, check Audit changes to its data checkbox as shown below-
After that, if you again refresh the Audit Report page, you will no longer see the error notification, and whatever changes you made in the security role table record, you will start seeing audit records for the same.
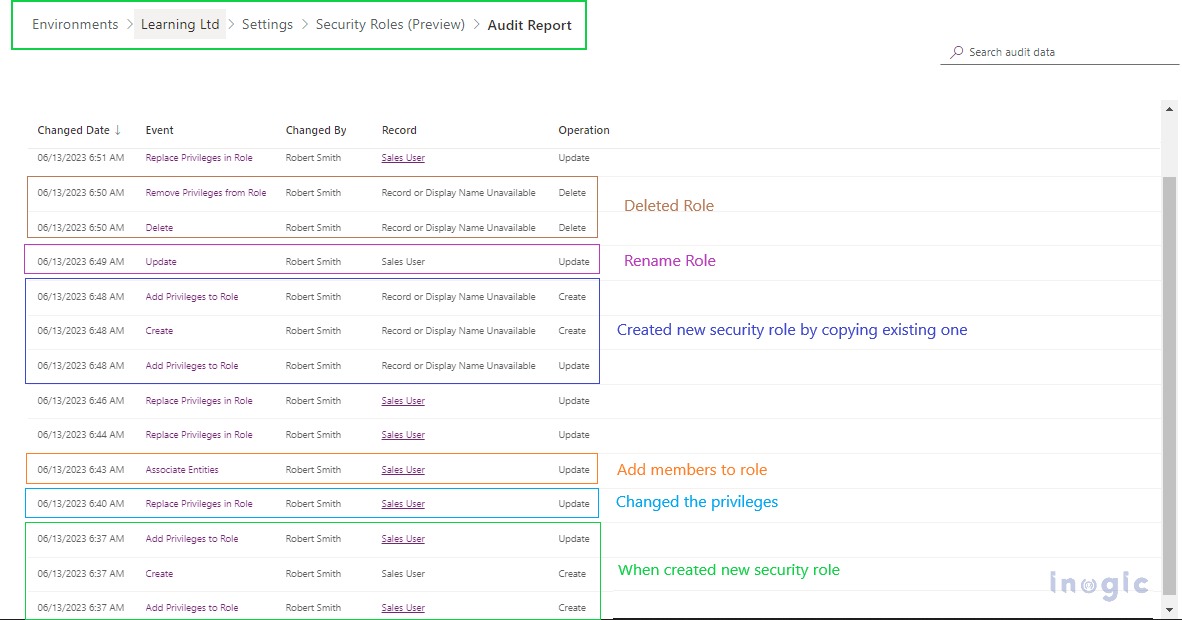
Below are a few examples-
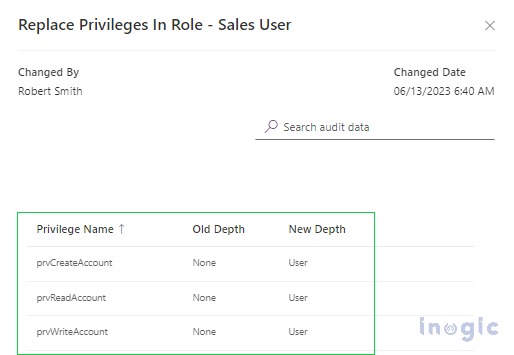
For more details, you can click on the Event column link. For example, on clicking Replace privilege in the Role event, we can see what privileges have been changed.
Conclusion
Thus, the Audit Report feature on the Security Role table in Dynamics 365 provides valuable insights and enhances the overall security management process by identifying any unauthorized modifications.