Introduction
While working on improving user account recovery scenarios, a common challenge often arises: how to securely allow a user to sign in and configure their authentication methods when their usual sign-in mechanisms (such as a mobile device or MFA method) are unavailable.
To address this, Microsoft offers a feature in Azure Active Directory (Azure AD) called the Temporary Access Pass (TAP), a secure, time-limited passcode that simplifies both the user and admin experience.
In this blog, we’ll provide a clear overview of TAP, explore its benefits, and walk through how to configure and use it effectively.
What is a Temporary Access Pass?
A Temporary Access Pass is a time-restricted, system-generated password that enables users to sign in and register their authentication methods — such as MFA or password-less sign-in — without needing access to existing methods.
This is particularly useful in the following scenarios:
- New employees setting up their account for the first time
- Users who have lost or changed their mobile device
- IT administrators assisting users who are locked out of their accounts
Essentially, TAP provides a temporary, secure gateway for accessing the system when usual authentication options are unavailable.
Key Benefits of TAP
The Temporary Access Pass offers multiple advantages:
- Prevents lockout situations due to loss of MFA devices
- Streamlines user onboarding and offboarding processes
- Enables passwordless authentication setup
- Reduces reliance on less secure backup methods such as security questions or SMS codes
- Highly configurable in terms of duration, scope, and usage policies
This feature supports a more seamless and secure user experience while reducing helpdesk overhead.
Configuring Temporary Access Pass in Azure AD
Setting up TAP involves two key steps: enabling the feature and issuing a pass for users.
Step 1: Enable TAP in Azure AD
1. Sign in to the Azure Portal
2. Navigate to Azure Active Directory → Security
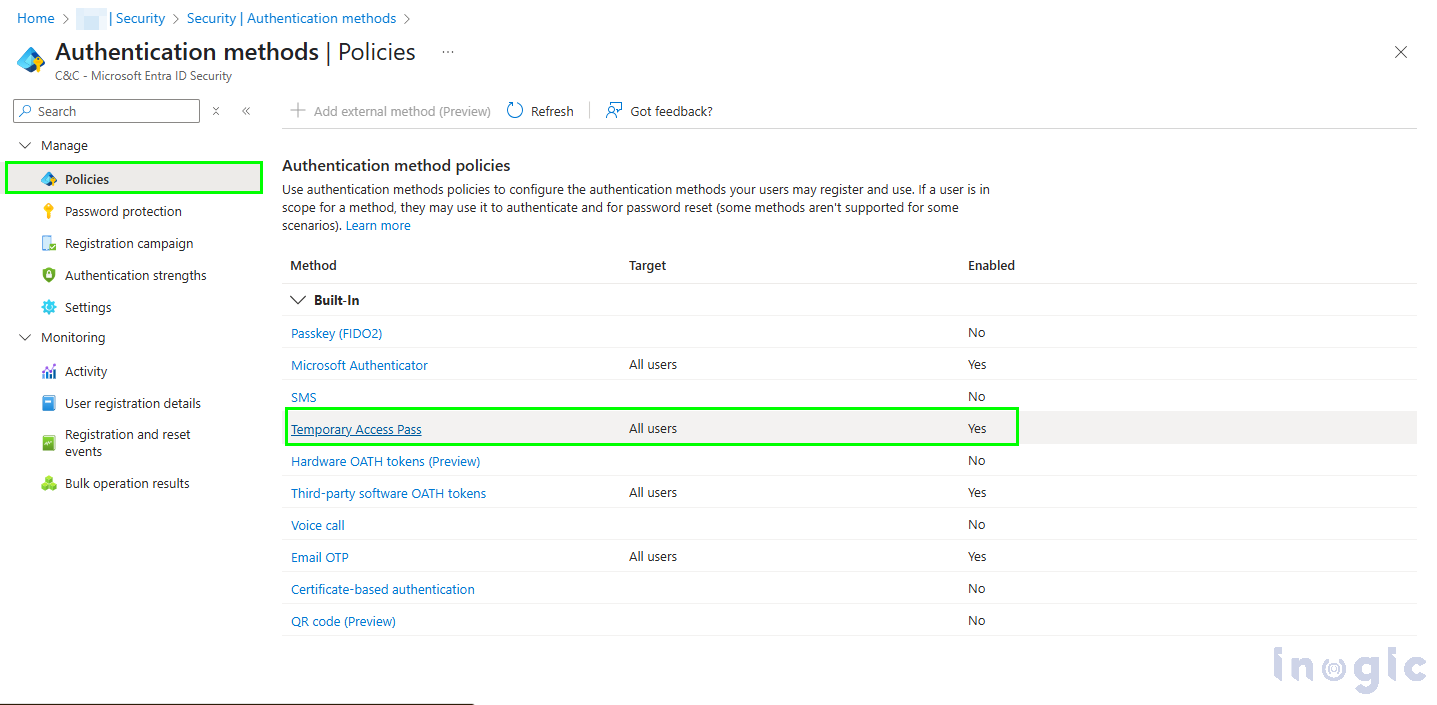
3. Under Authentication Methods, select Temporary Access Pass
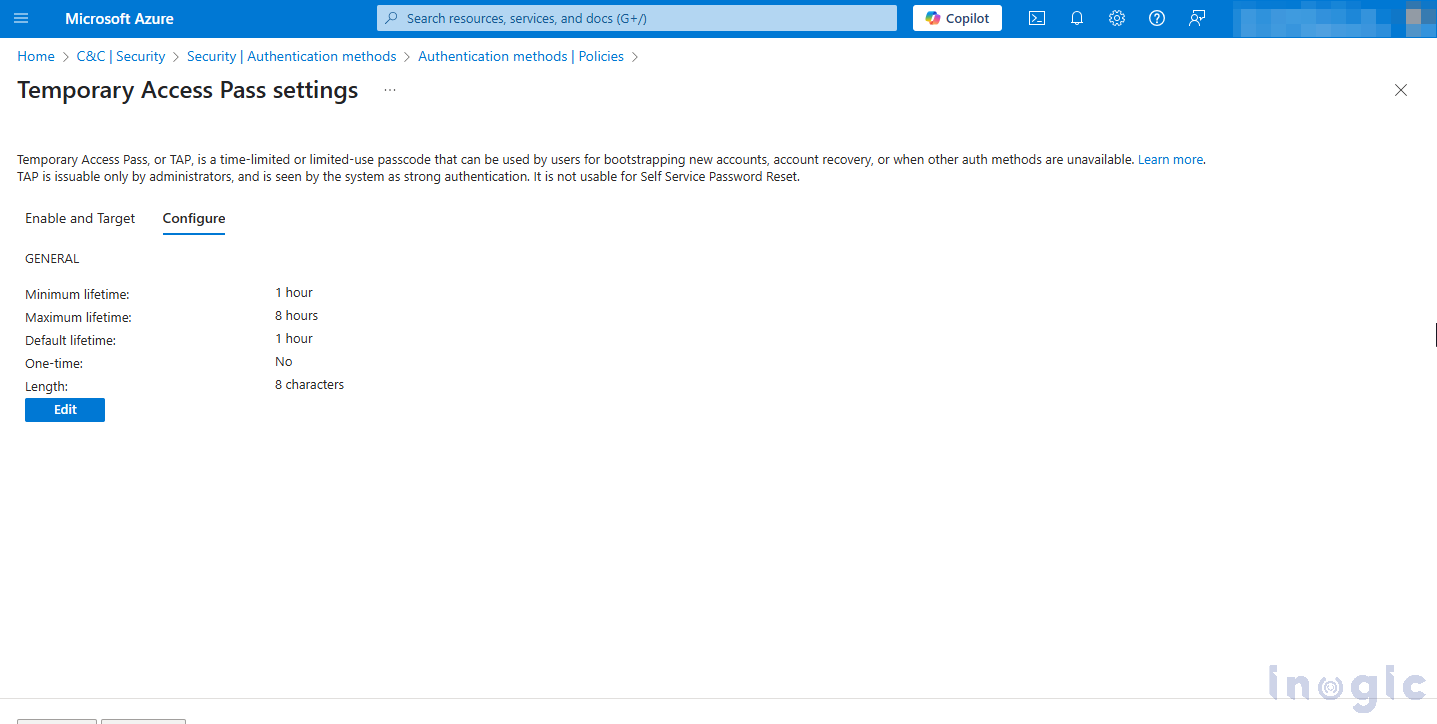
4. Click Enable and configure:
-
- Default pass lifetime (e.g., 1 hour)
- Single-use or multi-use configuration
- Targeted user groups (such as new employees or admin users)
Note: Begin with a test group before implementing organization-wide.
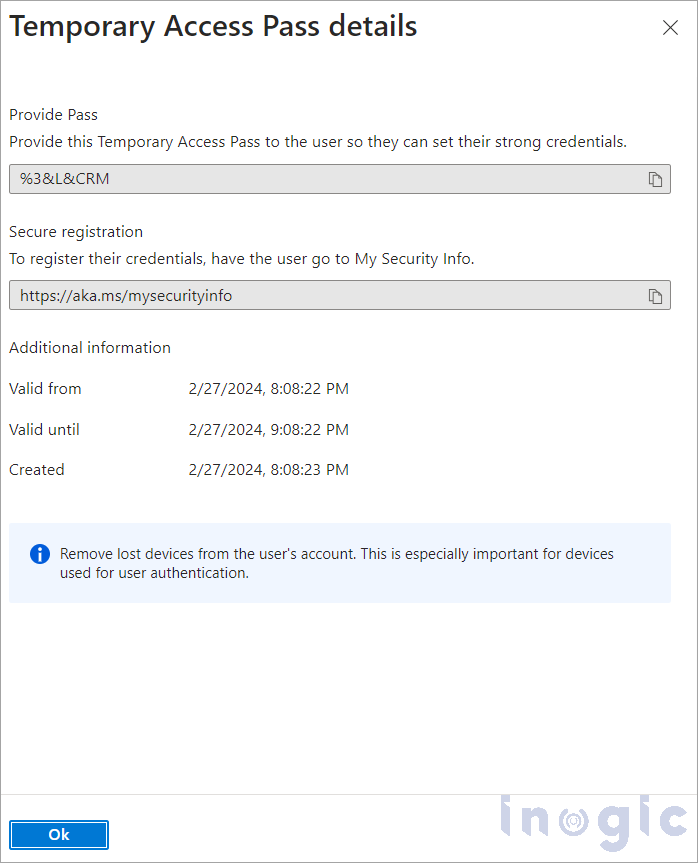
Step 2: Issue a TAP for a Specific User
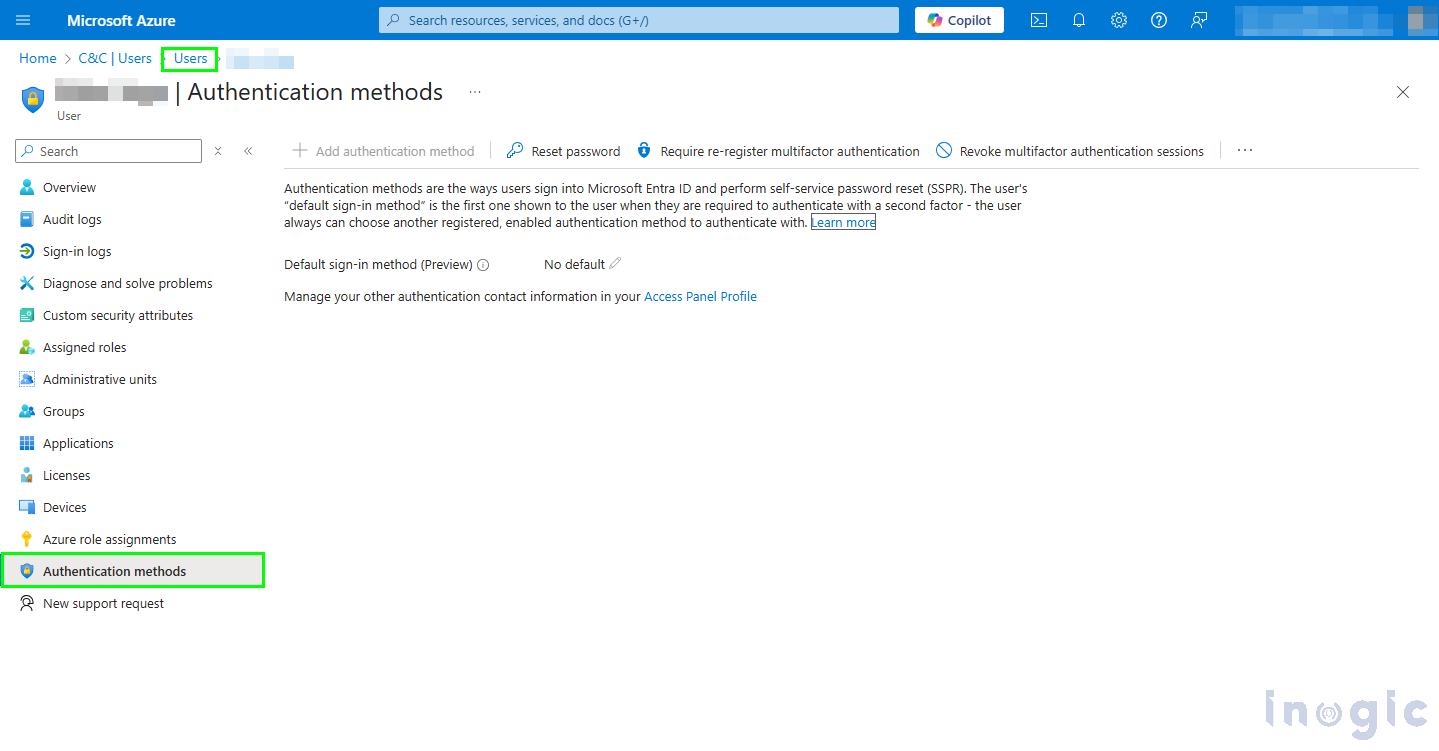
1. In Azure Active Directory, go to Users
2. Select the desired user and click on Authentication Methods
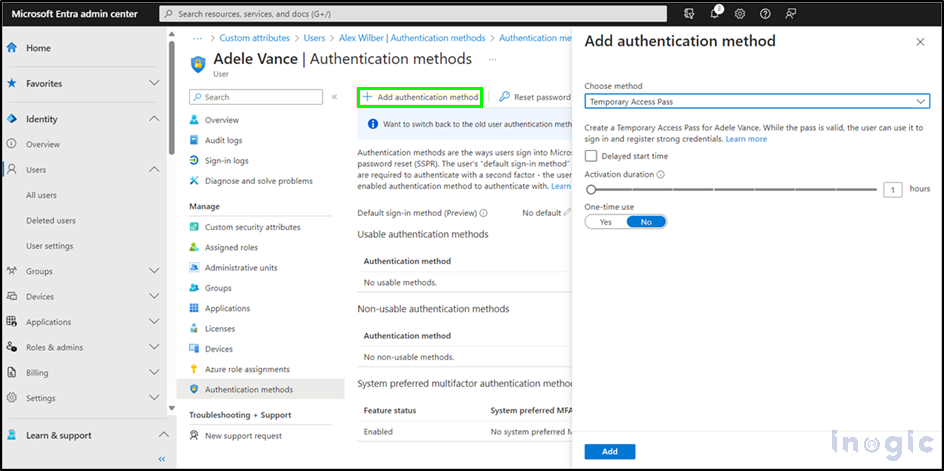
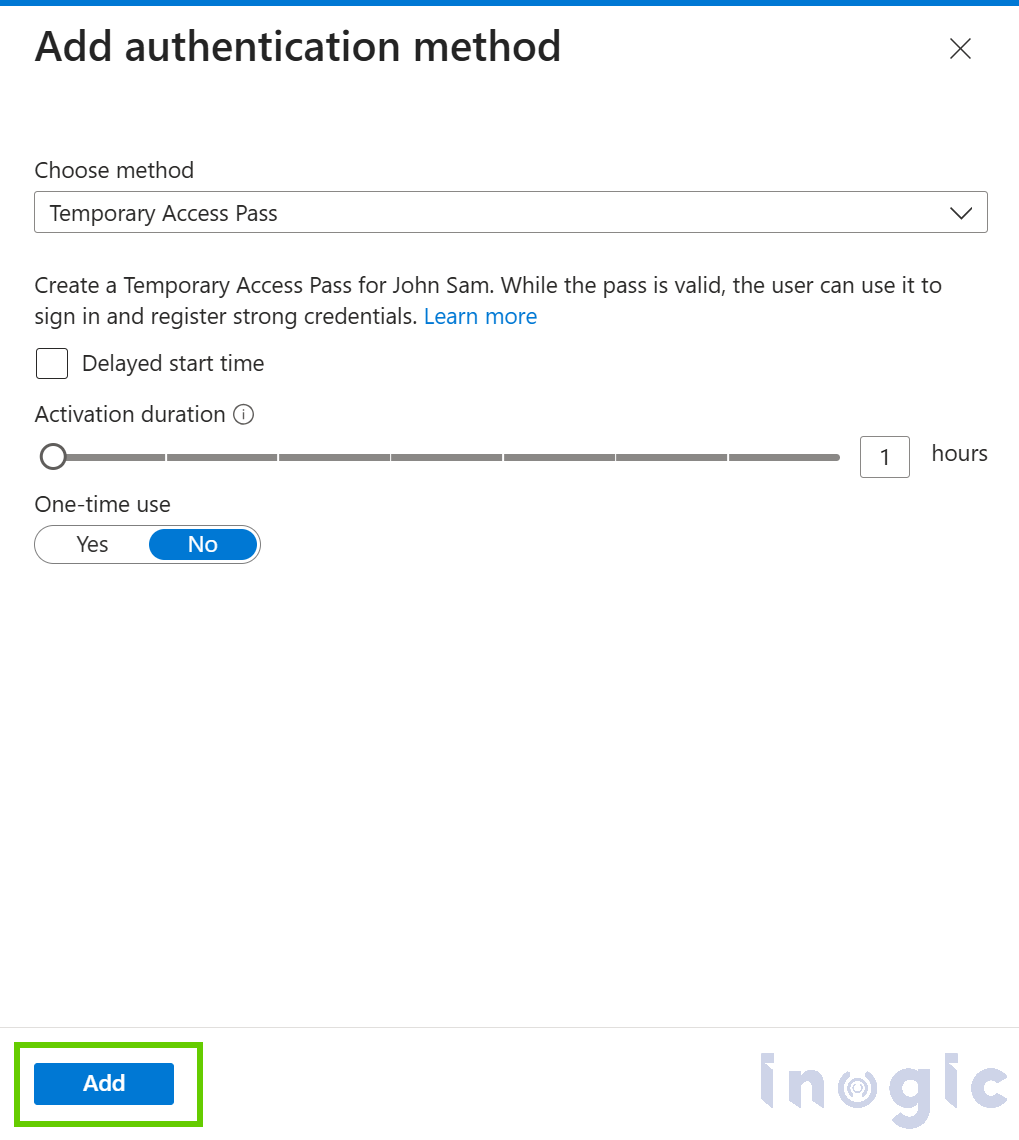
3. Click + Add authentication method and choose Temporary Access Pass
4. Define the expiration time and usage limit, once configured details will be displayed
5. Share the pass securely with the user (e.g., via a secure email or internal call)
The user can then log in using the TAP and complete their authentication setup without requiring previous credentials.
Scenario: A new employee is scheduled to begin work on a Monday morning. While their workstation is ready, they haven’t yet received their mobile phone. Normally, this would delay their access and require IT intervention. However, with TAP, a secure one-time pass can be issued in advance. The employee signs in, configures their authentication methods, and starts work without delay.
This small feature dramatically improves the onboarding experience and minimizes support bottlenecks.
Security Considerations
TAP is designed with security at its core:
- Time-bound and auto-expiring
- User-specific and non-transferable
- Fully auditable through Azure logging
- Allows policy-based customization based on your organization’s security needs
It is both a convenient and secure option for temporary access, fitting seamlessly into a Zero Trust security model.
FAQs
- Can a Temporary Access Pass (TAP) be reused multiple times?
Yes. TAP can be configured as either single-use (valid for only one sign-in) or multi-use (usable multiple times until expiry). The configuration depends on your organization’s security and onboarding requirements. - What is the maximum and minimum lifetime of a Temporary Access Pass?
The lifetime of a TAP can be set between 10 minutes and 30 days. Admins can configure the default duration and customize it per issued pass. - Does TAP work with passwordless authentication methods like FIDO2 keys or Microsoft Authenticator?
Yes. TAP is specifically designed to help users register or recover passwordless authentication methods. A user can sign in with TAP and then set up methods such as FIDO2 security keys, Microsoft Authenticator app, or Windows Hello for Business. - How is a Temporary Access Pass delivered securely to users?
Admins must share TAP securely outside the Azure AD portal (e.g., encrypted email, secure messaging, or direct call). TAP values are not sent automatically by Azure AD to prevent interception. - Are TAP events logged and auditable in Azure AD?
Yes. All TAP issuance, usage, and expiration events are recorded in Azure AD sign-in and audit logs, allowing administrators to monitor activity and meet compliance requirements.
Conclusion
The Temporary Access Pass may not be a high-profile feature, but it is one of the most practical tools available in Azure Active Directory. It simplifies onboarding, enables secure recovery, and supports the transition to a password-less environment, all while maintaining strong security controls.
If your organization is aiming to improve identity and access management, TAP is well worth exploring and implementing.